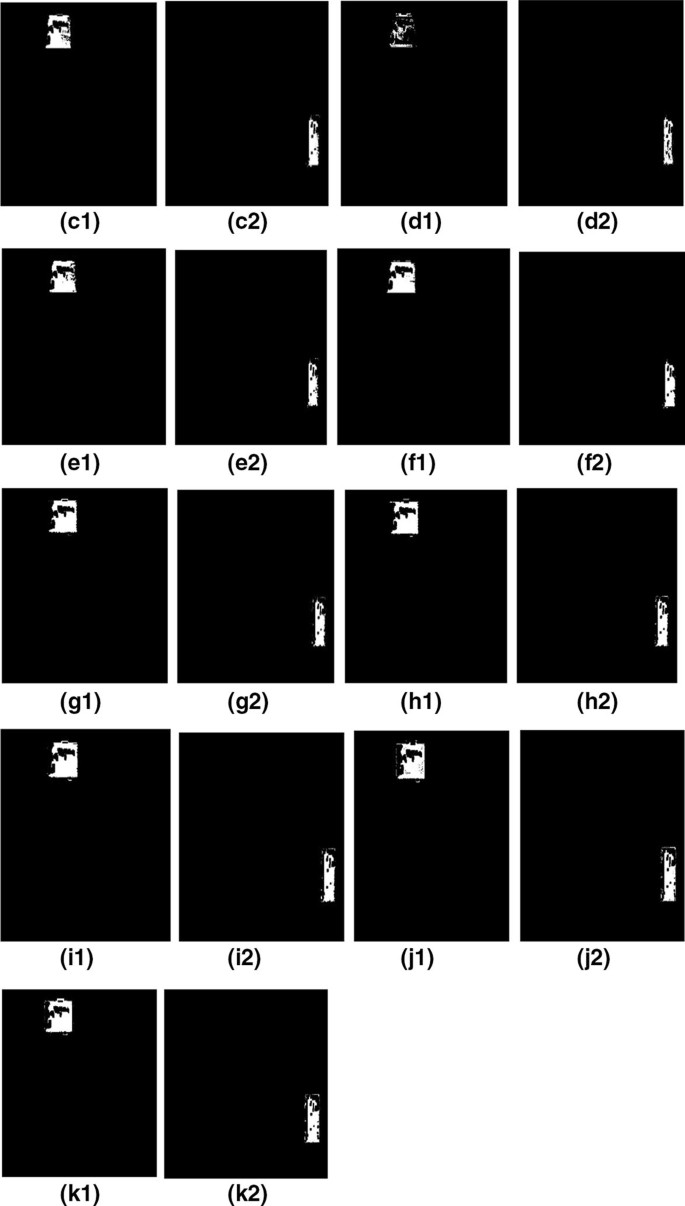
a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Last updated 14 setembro 2024


Week 1 — Copy Move Forgery Detection, by Eflatun Doğa AYDIN, BBM406 Spring 2021 Projects

a1), (b1), (c1), (d1), (e1), and (f1) shows forged images with plain

The first five examples for Copy-Move forgery detection: original
Copy-Move Forgery Detection Based on Discrete and SURF Transforms

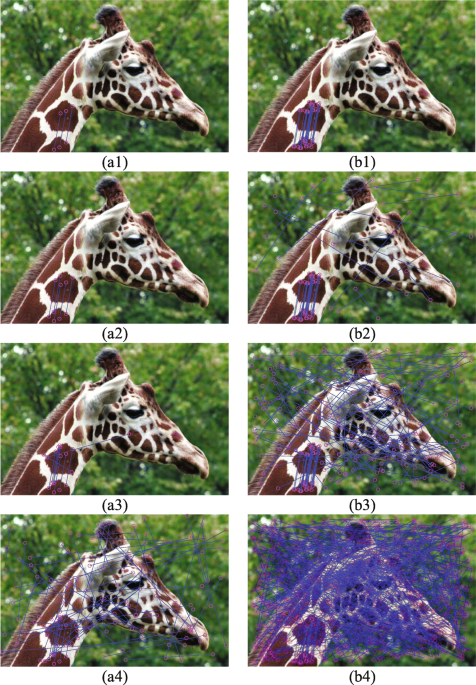
Example for copy-move forgery from [MS07] (original image left
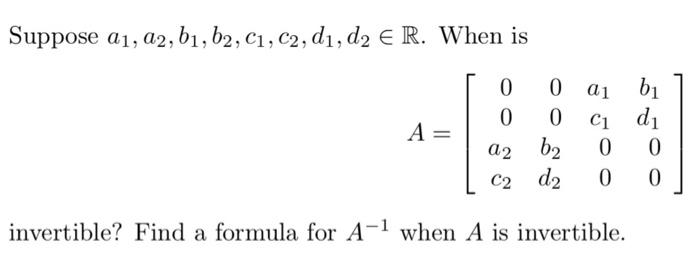
Solved Suppose a1,a2,b1,b2,c1,c2,d1,d2∈R. When is

Copy-move forgery detection using binary discriminant features - ScienceDirect

a1), (b1), (c1), (d1), (e1), and (f1) shows forged images with
Copy-move image forgery detection based on evolving circular domains coverage
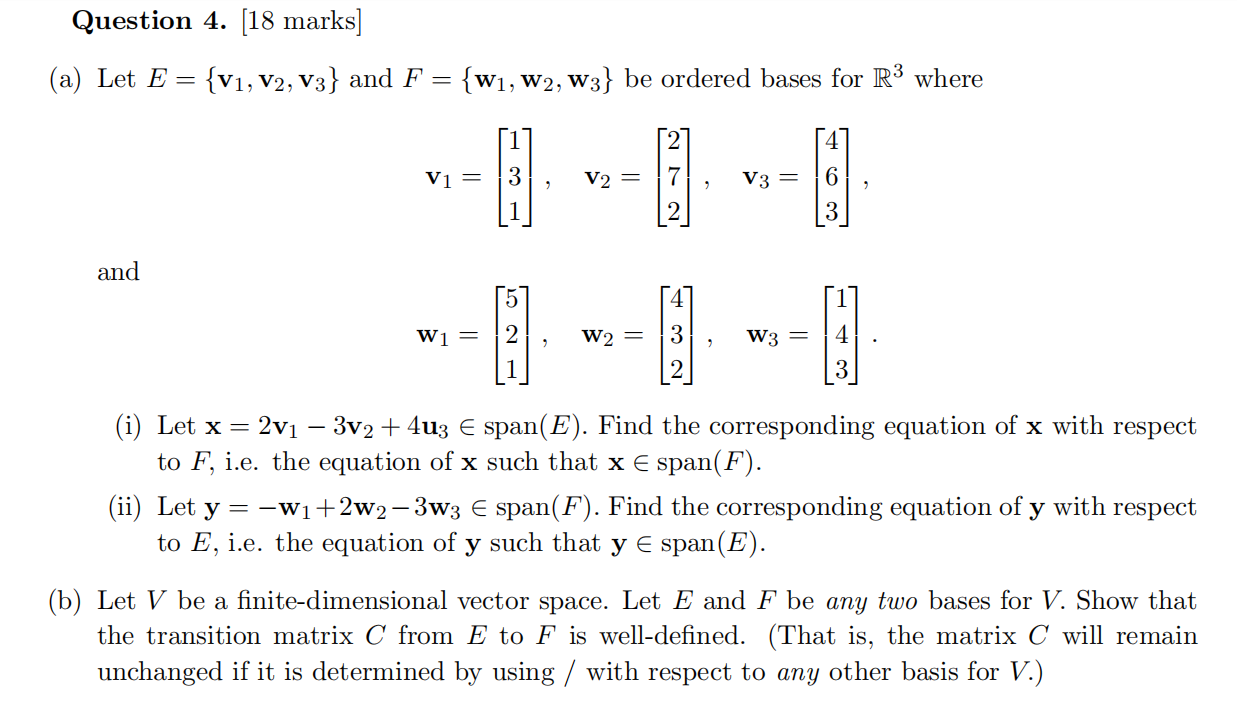
Solved Question 4. [18 marks] (a) Let E = {V1, V2, V3} and F
Recomendado para você
-
 G1/F1 System - Genera - 3D Printing & Additive Manufacturing14 setembro 2024
G1/F1 System - Genera - 3D Printing & Additive Manufacturing14 setembro 2024 -
 Transformers G1: Powerdasher F1 Dasher and Decoy #12 Skids14 setembro 2024
Transformers G1: Powerdasher F1 Dasher and Decoy #12 Skids14 setembro 2024 -
 Power HD Aluminum G1 High Stability Gyro Red For RC Car Drift F1 Touring On Road14 setembro 2024
Power HD Aluminum G1 High Stability Gyro Red For RC Car Drift F1 Touring On Road14 setembro 2024 -
 Filtrete F1 Room Air Purifier Filter, True HEPA Premium Allergen, Bacteria, & Virus, 12 in. x 6.75 in., 4-Pack, Works with Devices: FAP-C01BA-G114 setembro 2024
Filtrete F1 Room Air Purifier Filter, True HEPA Premium Allergen, Bacteria, & Virus, 12 in. x 6.75 in., 4-Pack, Works with Devices: FAP-C01BA-G114 setembro 2024 -
 F1: Lewis Hamilton Wins United States Grand Prix (PHOTOS) - Racing News14 setembro 2024
F1: Lewis Hamilton Wins United States Grand Prix (PHOTOS) - Racing News14 setembro 2024 -
 Griiip strikes first broadcast deal for disruptive race car series14 setembro 2024
Griiip strikes first broadcast deal for disruptive race car series14 setembro 2024 -
 F1 Miami Parking Guide: Official Pass & Unofficial Parking Lots14 setembro 2024
F1 Miami Parking Guide: Official Pass & Unofficial Parking Lots14 setembro 2024 -
 EBC Kawasaki ZX-6R (ZX 600 F1/F2/F3/G1/G2) 95-99 SRC Race/Sport Kevlar Series Clutch Kit - Sportbike Track Gear14 setembro 2024
EBC Kawasaki ZX-6R (ZX 600 F1/F2/F3/G1/G2) 95-99 SRC Race/Sport Kevlar Series Clutch Kit - Sportbike Track Gear14 setembro 2024 -
Solved Determine the appropriate relationship between f1(n)14 setembro 2024
-
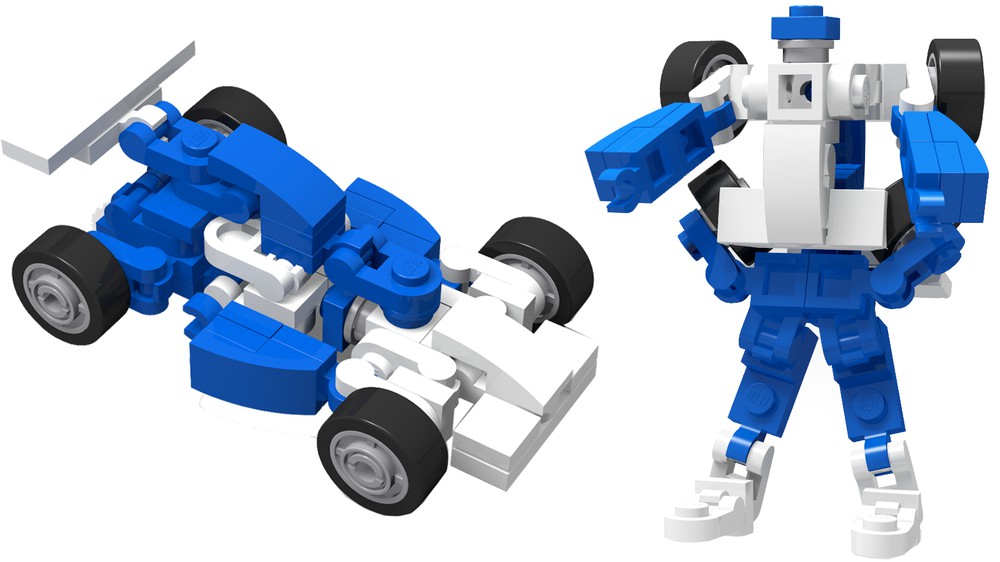 LEGO MOC Transformers G1 Mirage Mini Mecha by FreshBricks14 setembro 2024
LEGO MOC Transformers G1 Mirage Mini Mecha by FreshBricks14 setembro 2024
você pode gostar
-
 Compre agora o jogo G.I. Joe Operation Blackout para PS4 - Mídia14 setembro 2024
Compre agora o jogo G.I. Joe Operation Blackout para PS4 - Mídia14 setembro 2024 -
 Arquivos Sonic Boom - Música Instantânea14 setembro 2024
Arquivos Sonic Boom - Música Instantânea14 setembro 2024 -
 cursed crying emoji - Imgflip14 setembro 2024
cursed crying emoji - Imgflip14 setembro 2024 -
 Dublador português de Vegeta diz que nunca quis ofender o Brasil14 setembro 2024
Dublador português de Vegeta diz que nunca quis ofender o Brasil14 setembro 2024 -
 Unity 2019.4.9f1 - Toggle Show/Hide Gameobject with one keystroke. - Questions & Answers - Unity Discussions14 setembro 2024
Unity 2019.4.9f1 - Toggle Show/Hide Gameobject with one keystroke. - Questions & Answers - Unity Discussions14 setembro 2024 -
 Roblox Robloxclothingpic - Twitter - Com25d7hnmt5q - Template14 setembro 2024
Roblox Robloxclothingpic - Twitter - Com25d7hnmt5q - Template14 setembro 2024 -
 Resident Evil 4 Remake Garrador for GTA San Andreas14 setembro 2024
Resident Evil 4 Remake Garrador for GTA San Andreas14 setembro 2024 -
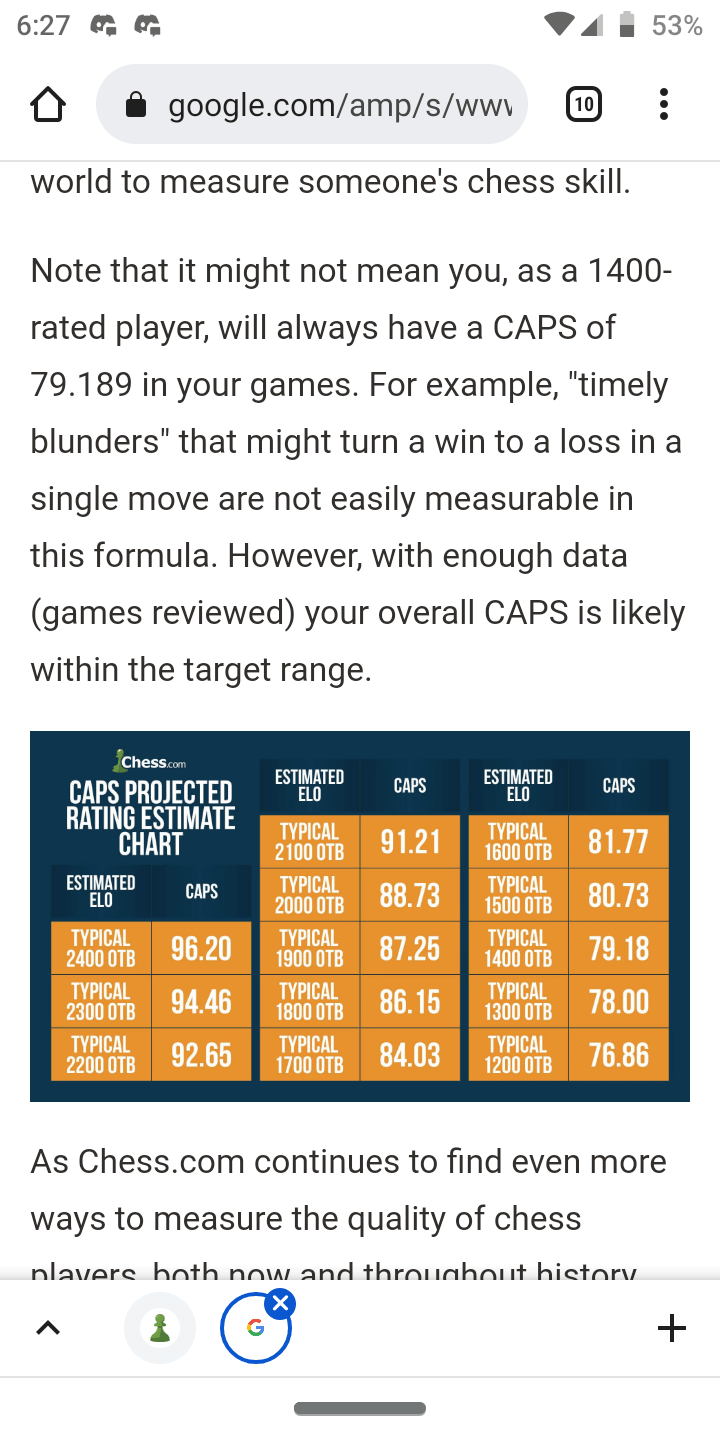 What is the expected accuracy for rapid chess? - Chess Forums14 setembro 2024
What is the expected accuracy for rapid chess? - Chess Forums14 setembro 2024 -
 Valorant 5v5 Bracket Tournament – Online – Elite Gaming Arena14 setembro 2024
Valorant 5v5 Bracket Tournament – Online – Elite Gaming Arena14 setembro 2024 -
 Pastoral constitution on the Church in the modern world by Vatican Council (2nd 1962-1965)14 setembro 2024
Pastoral constitution on the Church in the modern world by Vatican Council (2nd 1962-1965)14 setembro 2024